Twits beware.
Twitter phishers and spammers are out on the prowl, and more than a few unsuspecting educators have fallen prey to their clever ruses and hacks in the last two days. The posts on the official Twitter blog “Gone Phishing” from Saturday and “Monday Morning Madness” from today provide more insights. Even Barack Obama’s Twitter account was hacked. I wrote the post “Avoid Twply.com and change your Twitter password frequently” last Friday, and that advice appears to be quite timely.
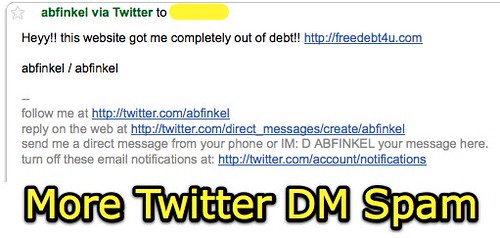
I received “Twitter spam” today from four different educators whose Twitter accounts were compromised in some way, either by a phishing scheme, a website with malicious operators which solicits Twitter credentials, or hackers. What are the lessons learned here?
- Use a secure password on your twitter account and change it periodically.
- Be VERY wary of EVER putting your twitter password into a website that isn’t the official Twitter site, or into a program you run on your computer or handheld that you can’t verify to trust. Just like bank and credit card phishing schemes, people are now phishing with fake twitter sites, so beware of links to Twitter you receive in email.
- If your twitter account has been hacked, try to login and change your password to something secure immediately. Then follow the above suggestions to KEEP it secure and private. If you have lost control of your twitter account, then contact the Twitter support team directly for assistance.
I blocked the user accounts from which my Twitter spam originated today, and appear to have been compromised. I am hoping that will mean I won’t receive further twitter direct message spam messages from their accounts. So far, so good. I also tried to contact the individuals whose accounts were sending spam either via email or leaving comments on their blogs or social networking pages. 3 of the 4 people included website links in their public Twitter profile, so I was able to attempt electronic contact to give them a heads up. One person said she’d been inundated with emails from friends about it, because evidently they had also received the spam direct messages via Twitter. She hadn’t used her Twitter account in four months, since August, so I’m not really sure how someone managed to take control of her account.
Alan Levine touted praises for “Andy M’s Yahoo Pipe for putting your twitter followers locations on a map” this evening, but with all these examples of Twitter phishing I’m reluctant to put my Twitter credentials into ANY website other than Twitter.
Anyone have suggestions on how to decide which new websites to trust with your Twitter credentials, and which ones are better to avoid? I’m thinking the conservative path of not trusting ANY of them with Twitter credentials (including a password) is the best policy. I still am going to keep using Twitter Karma, however, unless I hear or read of a problem with it– I LOVE its functionality and haven’t found another site to match it yet.
Most people probably need some reminders and proddings to follow good password security procedures. The Joomla Installation Guide (PDF) by Andy Wallace includes a list of guidelines as good as I’ve seen anywhere regarding password security. On page 13 under “Secure Password Thinking” he writes:
Any password you create for Joomla!, MySQL, Apache, or in fact any passwords you ever create should be
made as secure as possible.Typically this would mean:
- using a minimum of 6 characters -the more the better but 8-10 should be an ideal
- a mixture of upper and lower case alphabet characters, numbers, and permitted special characters
for example -, _, *, $, !, %, although the use of these may be governed by the host settings on
shared or virtual hosted, remote servers- do not use easily identifiable passwords for example, birthdays, children’s or family names or words that could be easily associated with you
- in fact try not to use real words at all, replace letters with their numeric equal so the word ocean could become 0c34n (yes – I know it is a real word and there are only 5 characters but it is just an
example) try 0c34n!c – and no do not now use that either- another way is to think entirely off-the-wall. Think of a favourite novel for example, The Hitch-hikers
Guide to the Galaxy, and then take say the first and last letter from each word giving a sequence of
letters (as indicated by the underscores):
Example 1. t e h s g e t o t e g y
this clearly means absolutely nothing but it could still be traced – eventually – by a determined
cracker so let us mix it up a bit more:
Example 2. T 3 h $ 9 3 t 0 T 3 g Y
but you can now see that it would be a pretty illogical logic that would need to be applied to even
come close to cracking that and when the additional security features of the various platforms is then
laid over the top of this – we would not want to say it is impossible to crack, but they would take a
very long time, and of course you should regularly change your passwords anyway.- if you keep a written record of your passwords always ensure they too are kept secure and safely out
of the way of prying eyes- despite the temptation, try to avoid using the same password for all your various access
requirements, both at home and at work
When I went to work for AT&T in 2006 I was amazed and a bit shocked how many different passwords I had to create for different accounts, and how often I was forced to change them. In many cases, employees were/are FORCED to use secure passwords and change them often. This is not popular, but it is smart, both for organizations and for individuals.
It’s time for us all to “act smart” when it comes to password security, for Twitter and for other sets of login credentials. The next time someone takes you on a fishin’ trip, make sure it’s the kind that starts with “f” and not “ph!”

![]() photo credit: mohd fahmi
photo credit: mohd fahmi
Technorati Tags:
twitter, phishing, hacking, password, security
If you enjoyed this post and found it useful, subscribe to Wes’ free newsletter. Check out Wes’ video tutorial library, “Playing with Media.” Information about more ways to learn with Dr. Wesley Fryer are available on wesfryer.com/after.
On this day..
- Share Podcast Excerpts using Audacity, iMovie and Google Slides – 2020
- We Need More Curious Dreamers, Tinkerers and Makers – 2016
- Best Free iPad Apps for Stopmotion Movies – 2016
- Why I Switched My WordPress Web Host from WP Engine to Site5 – 2014
- Optimize a Google Site for Mobile Accessibility and Metrics – 2012
- Photo 365 Projects on Seedlings: Thurs Jan 6th – 2011
- Upset about Standardized Testing (Love Letter To Albuquerque Public Schools) – 2011
- Powerful Ingredients Videoconference today – 2010
- Access your notes even after your textbook subscription expires – 2010
- Copyright-friendly image source websites – 2009

Comments
4 responses to “A whole lotta Twitter phishin goin’ on”
There seems to be a lot of new sites popping up that don’t really give you too much information until you register. Nice, graphically appealing main page with a great tagline, but that’s it. For me, that’s a red flag right there.
I don’t think abandoning them all is the answer either though. If an app gives plenty of information, FAQ’s, contact information, etc. before you sign up, then I think it’s reasonable to think the site is ok.
I agree with you, though. We are very complacent when it comes to changing and using cryptic passwords. Do you know when most people put burglar alarms in their homes? Yep, AFTER they’ve been victimized.
This is a good wake-up call for us all.
On the other hand, c’mon, it is not like twitter being compromised is anywhere in the ballpark of your bank account. I’m haivng trouble recalling all the places my twitter credentials are sitting- wordpress plugin (to send posts to twitter), facebook (for twitter to FB status), twitterfeed (to pull RSS content into twitter), tr.im a nice URL shortening service… If you are going to be that guarded and never put a username/password into a web site, well you might was well stay home and just knit sweaters.
That said, the twitter authentication appears to me as weak as that 2 month old stalk of celery in the back of my fridge. Compare how it deals with third party apps and more robust services like flickr (where you authneticate any third party use), Yahoo services, facebook apps, etc. Twitter’s security is very very thin.
Alan: I agree, bank and credit card fraud/phishing is HUGE and Twitter exploits are not apparently taking place at a scale that even approaches that. The stakes and benefits of a Twitter hack is much different!
I also agree it would be an overreaction to not use any web-based twitter services. As I said, I’m still using Twitter Karma, and I love its functionality.
The issue this raises, however, is an important one. How should people evaluate the trustworthiness/viability of a website before entering Twitter credentials? Lee is on the right track that the provision of privacy info, info about the developers, etc. is a good sign. A website like twply which simply says (literally) “Your password is safe with us. No worries!” should be suspect. Beyond that, however, I think it gets fuzzy quickly trying to determine what website to trust.
I am not a developer with the expertise to fully explain and understand this, but I understand some twitter services are able to function without having users enter their passwords. Hopefully Twitter will develop a scheme of more secure authentication which will permit developers to not have to solicit passwords to offer new web services. The advent of more secure authentication schemes will not stop phishing emails, of course, or reduce the importance of using secure passwords and changing them frequently.
See your replacement of letters with numbers reminded me of the “Leet” alphabet or “Leetspeak.” (I forget were I first came across this. maybe wired magazine.) See: http://en.wikipedia.org/wiki/Leet
I guess some technology savvy people use this “Leet,” so one might want to avoid number substitutions that match “Leet” for a more secure password.