The more we rely on userIDs and passwords to verify our identity online, the more susceptible we are to attacks by people who, for different reasons, want to harm us or take control of our digital accounts. Several recent cases of hacked accounts highlight the need for greater personal account security and information security overall. These are not cases of older adults who lack digital saavy and literacy: These are articles written by highly connected netizens who have been successfully targeted (for different reasons) by malicious hackers exploiting security vulnerabilities in different online accounts. I highly recommend you take a few minutes to read the articles highlighted in this post and consider ways you can further secure your digital life immediately. At the end, I’ll share 10+ “lessons learned” and suggested advice.
The first article you need to read, if you haven’t previously, is Mat Honan’s August 2012 article in Wired, “How Apple and Amazon Security Flaws Led to My Epic Hacking.” Basically a hacker was able to convince support representatives on the phone, working for both Apple and Amazon, to give up enough information to devastate Mat’s digital life in just an hour. The opening paragraph of his article should get your attention. Mat wrote:
In the space of one hour, my entire digital life was destroyed. First my Google account was taken over, then deleted. Next my Twitter account was compromised, and used as a platform to broadcast racist and homophobic messages. And worst of all, my AppleID account was broken into, and my hackers used it to remotely erase all of the data on my iPhone, iPad, and MacBook.
The second article you need to read is “How I lost my $50,000 Twitter username” by Naoki Hiroshima. My wife saw and shared this on Saturday using Flipboard, thanks to a tweet by Jonathan Wylie. It’s also available on Gizmodo. In Naoki’s case, a hacker gained access to his domains and domain-based email using social engineering techniques with a phone support person at GoDaddy. He was then able to extort/force Naoki to give up his TwitterID.
The third article to read is “How I almost lost my $500,000 Twitter user name @jb… and my startup” by Josh Bryant. Josh’s article references both Mat and Naoki’s situation, and although it has a more positive ending it also highlights more account vulnerabilities hackers can and are using.
Here are some “lessons learned” from these three cases and suggested advice we can follow to try and avoid becoming digital account hack victims.
1. Do Not Save Online Credit Cards
Saving credit cards to use online again on different websites seems to make sense. It can make future transactions faster, and still requires your userID and password to make a purchase. What could be the potential harm? The answer is: A lot. Since some companies will let callers verify their professed identity by giving the last 4 or more numbers of their credit card, it’s possible a phone representative could share those numbers with an account hacker.
Don’t save your credit/debit cards online with any website.
2. Don’t Post Your Email, Phone or Address Information Online
According to Mat Honan’s story referenced previously, all a hacker needs to gain access to many web accounts is your billing address and the last four digits of your credit/debit card. We hear a lot of hoopla over privacy and how it’s being lost today, and some people wonder, “So what?” Here’s what: When people who want to harm you can gather personal information about you, this can provide them with more ammunition to hurt you. Posting your main email address ANYWHERE online increases the amount of spam you receive, but it also can open you up to security hacks. I’ve used a PObox account for years to share a working (but not primary) email address online, since I first saw Larry Lessig using it on his website. I use a physical PO box as my public mailing address, as well as the address where I register my web domains. Josh Bryant recommends ALWAYS using a “private Who-IS” domain registration optional service. Never post your actual address / billing address to any websites, email groups, etc. Keep all this information as private as you can.
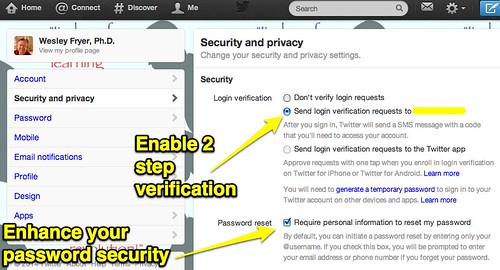
3. Enable Two Step Verification Whenever Available
Two step verification is a security requirement in which a user has to provide a number (often a code sent via SMS to their cell phone) in order to gain access to an account or system. When I worked for AT&T as an education advocate from 2006-2008, the company issued all employees an “RSA ID” which regularly changed numbers. We had to enter our RSA ID to login to the corporate network, thereby proving (with a physically controlled and verified ID) we were ourselves. Two step verification basically does the same thing, except websites can use cell phone text messaging. Both Google and Twitter now support two step verification. Change your account settings immediately, if you have not already, to enable this. Enable two step verification on every website you use, if it is available.
4. Shred All Credit Card / Debit Card Receipts
Did you think your debit and credit card receipts were devoid of information malicious hackers could want since they only include the last four digits of your card number? Think again. Those four digits can be used to spoof your identity. Shred all your credit card / debit card receipts.
5. Obtain New Debit / Credit Cards Regularly
Consider asking your bank to issue you new debit and credit cards more often than they expire. The more you use a card, and the more it’s “out there” on different websites and in saved databases, the more chances there are that someone who is not authorized to used the card will get the numbers.
6. Use a Password App
For years I held off using an app on my iPhone to save passwords, even though my parents (and others) encouraged me to do this. Finally I gave in over the holidays this year and started using MSecure. Consider using it or something similar. The app can also generate random passwords for different web accounts. And yes, you NEED to use different passwords on the different accounts you have. Do NOT just use a single / common password. Doing so will further open you up to exactly the sort of attacks highlighted in this post. See Twitter’s Help Center article, “Keeping your account secure,” for a host of excellent suggestions relating to password security and other issues.
7. Don’t Login to non-SSL WordPress Sites on Shared WiFi Hotspots
Most WordPress sites and some other websites don’t use SSL encryption to hide your passwords when you login to the site. Since your userID and password are sent “in the clear,” anyone using the same wifi hotspot as you (like a coffee shop hotspot) and free packet sniffer software can see and capture your login credentials very easily. The Firesheep extension for FireFox demonstrated this dramatically several years ago. Read my November 2010 post, “Firesheep should get your ATTENTION: Open Public Wifi Dangers are REAL,” for more background. For a visual explanation of this, watch the 3 minute screencast I created in March 2013 using the iPad app Ask3, “How Can Someone Hack Your Website in a Coffee Shop?”
8. Don’t Use a Domain-based Email Address for Website Access
Naoki Hiroshima recommends using a Gmail email address or other non-domain specific email address for accessing your websites. In his case, a hacker gained control of his email account by taking over his GoDaddy account. Josh Bryant points out this is not a guarantee of protection, but it does make sense to do if you’re using a personalized email account based on a domain you own. Naoki also recommends changing the “TTL for the MX record” of your domain to a longer time interval. In a hacking situation, this would give you more time to access your domain before it’s switched over to a malicious hacker’s control. If you’re not managing your own domains these recommendations won’t be relevant, but if you DO have your own domain you should consider them.
9. Use a separate Amazon account for your AWS services and shopping
Amazon encourages users to have a single account for their cloud services and for personal shopping. Josh Bryant recommends otherwise. It may be easier for hackers to gain access to your personal shopping account, but if they do and you have your cloud services connected to the same userID you are more vulnerable to attacks.
10. Consider Private Who-Is Domain Registration
Josh Bryant recommends always using private “Who-Is” domain registration. This means instead of listing your personal address when someone looks up the owner of a particular web domain, a third-party company will be listed who has your information on file. If law enforcement or another legitimate party needs to find out who owns your domain, they can, but the general public can’t just look up that information readily online. The disadvantage is this costs an additional fee per year if you opt to use it. Josh considers those costs worthwhile.
11. Set a SMS Email Alert for “reset password”
I use SMS text alerts in my primary Gmail account for several different things. Each of the hack stories highlighted previously involved time-critical actions taken by both the hackers and the hacked. Consider setting up a custom mail filter in your Gmail (or other email service) so you’re notified whenever a password reset message is received. This could get irritating if you have a popular account that lots of people try to hack regularly, but it also could provide you with the alert time you need to take action if someone is actively (and successfully) gaining access to one or more of your web accounts. Based on the stories of these three hacking victims, it sounds like the best thing to do if you’re in the middle of an account hack is call the company yourself and request that your account be locked from phone changes.
12. Get a “Chip and PIN” Credit/Debit Card As Soon as Possible
The January 23, 2014, NPR article, “Target Hack A Tipping Point In Moving Away From Magnetic Stripes,” highlights how the rest of the world (outside the United States) has moved beyond simple “magnetic stripe” credit and debit cards. The rest of the world has embraced more secure electronic payment systems using a “chip and PIN” system, and this will be coming to the USA soon. Ask your current bank to notify you when a “chip and PIN” debit/credit card is available, and start using one as soon as possible. It will take years for all the point-of-sale locations in the United States to upgrade, but it sounds like this transition is both needed and inevitable given current security vulnerabilities with our magnetic strip payment cards.
Can you think of other lessons learned, recommendations, or pieces of advice to offer others when it comes to online account security and information security? I hope these articles and ideas are helpful to you. If so, please let me know via a tweet to @wfryer or a comment here.
Technorati Tags: password, security, hack, account, privacy, two, factor, authentication
If you enjoyed this post and found it useful, subscribe to Wes’ free newsletter. Check out Wes’ video tutorial library, “Playing with Media.” Information about more ways to learn with Dr. Wesley Fryer are available on wesfryer.com/after.
On this day..
- The Council of Constance and Modern Web – 2021
- American Revolution Videos from Schoolhouse Rock and Discovery United Streaming – 2014
- Cross Examination Debate Flow Template for Numbers in iWork ’09 – 2012
- Teach Your Students to be Digital Artists (and learn from Kevin Honeycutt) – 2012
- Blog comment moderation: How and Why? – 2010
- Crescent Public Schools: The Eyes of Oklahoma Are Upon You! – 2010
- Present at OSSBA in August 2010 – 2010
- eDiscovery requirements and archiving student email – 2010
- iPhone iTalk Application: A Great Event Recorder – 2009
- Comparing Broadband USB Options for Laptops – 2009



Comments
One response to “Hacker Cases Highlight Need for Greater Personal Account and Information Security”
[…] Hacker Cases Highlight Need for Greater Personal Account and Information Security | Moving at the Speed of Creativity […]