DISCLAIMER: ALL THE IDEAS BELOW ARE EXPRESSLY SHARED WITHOUT ANY TYPE OF WARRANTY WHAT-SO-EVER!
I helped some friends yesterday get a wireless router connected to their home high speed DSL modem, and learned an important difference when connecting a DSL modem to a router compared to a high speed cable modem. These details can vary by service provider, but may be of interest and helpful if you are doing this sort of thing. Full disclosure: We would have a DSL high speed connection at our house instead of a cable connection if we could, but unfortunately we live two blocks too far away from the central office or DSL sharepoint to get it. So, as we did in Lubbock, we have a home cable modem connection.
Both a DSL and a cable high speed internet connection use a “modem” to connect the user’s computer or network to the Internet. The cable modems I’ve used and configured in the past, however, do not use any type of userid and password to log into the network and get online. Instead, the cable modem has a MAC address and is “provisioned” by the local cable company to be authorized to connect online from a particular street address. When we moved from west Texas to Oklahoma, we were able to use the same cable modem we had obtained previously but had to call and get it “provisioned” by the local cable company to get online in our new location– which was a different part of the residential cable network. Same company / ISP, but a different network segment.
When a cable modem gets online, it uses the MAC address of the first device connected to it and gives a live, global IP address to that device. For people running Windows-based computers, this is and has been an extremely hazardous configuration because of the proliferation of malware that spreads organically to other Windows-based computers (primarily) connected to the Internet. The Security Now! Podcast episode #47 on “Internet Weaponry” gives an extensive and eye opening account of how our present state of malware attacks evolved over time. It is so bad currently that if someone connects an unpatched computer running WindowsXP service pack 0 (neither service pack 1 or 2) directly to the Internet with a high speed connection in the United States (and possibly elsewhere), they will generally get infected with malware in less than two minutes without doing anything– without browsing to any websites, receiving any email attachments, etc. We live in a hostile computing environment, particularly for Windows-based computers. (In my mind, this makes the decision to primarily use either Macintosh or Linux-based computers even more of a no-brainer today!)
Regardless of what operating system you are using, it is a good idea from a security standpoint to connect your high speed modem directly to a router instead of directly to your computer. I have used and recommend Linksys routers, but there are many brands and most function the same at the low end of the spectrum. Today in the central US where I live, you can obtain a wireless router (which also lets you get your laptop computers and other devices like DVRs online wirelessly) for less than $50 US. This is what the router I was helping my friends configure looks like, and is the same as the one I currently use at home. It is a Linksys Wireless-B router. Wireless-G routers and now Wireless-N routers are available, but the higher transfer rates of the newer protocols really just have effect if you share files within your local network. Wireless-B routers have a top speed of 12 MBPS, and that is still faster than most cable modem and DSL modem top speeds:
There are several advantages of connecting a high speed Internet modem directly to a router. The primary benefit is that this configuration places all the computers at your home behind a firewall. Technically speaking, your router serves as a NAT router, which results in the creation of a private network at your house where each device (computer or other) has a LOCAL rather than GLOBAL IP address. The firewall effectively blocks all the “Internet noise” that can infect Windows-based computers (primarily) with malware. Again, listen to Security Now! Podcast #47 for much more detail on this. If you are going to do special gaming applications or H.323 videoconferencing on your home network, you may have to do some special port forwarding configuration on your router or give your videoconferencing unit an IP address designated as the DMZ of your network, but for most people today Internet browsing and email are their primary activities and these don’t require any special router configuration.
One exception to this involves third party email programs configured to use SMTP. Many internet service providers (ISPs) including Cox Communications, block port 25 Internet traffic. Port 25 is commonly used to send email through something called an SMTP server, and port 25 traffic is blocked again because of malware prevalence: Many Windows-based malware programs create a local SMTP server and spam others from the infected computer. By blocking all or unauthenticated SMTP traffic on port 25, ISPs are trying to fight spam. If you use a webmail interface this is not a concern, but if you use a third-party email application like Eudora (yes, I have some family and friends who still are Eudora users) or other programs– and aren’t doing something fancy like logging into a corporate VPN, this can be a problem. Generally you have to reconfigure your email program to use the SMTP server settings specific to your ISP. The easiest workaround for this is to just use webmail, but I continue to use third-party email programs so this has been an issue for me as I get online different places. This SMTP mail issue does not affect router configurations, however.
Here is the main problem many people fall victim to when they configure a wireless router at their home: They fail to configure wireless security settings.
People often fail to change the default settings on their wireless router, and this effectively permits anyone in the neighborhood who wants to (and is in the approximately 300′ range of most wireless routers) to use their Internet connection. This many not be a problem, and some people don’t really care, but if the person does major file downloading via your connection it could take noticeable bandwidth away and negatively affect your own use of the Internet by slowing things down. Perhaps less likely but none the less an issue of concern, if an Internet-borrowing neighbor does anything illegal while online using your wireless connection, authorities would trace the suspicious/illegal activity to YOUR address. It is a good idea to take at least some basic steps to secure a residential wireless Internet connection.
Cable modem connection
In the case of the cable modem connections I’ve used in the past, no only special configuration of the cable modem is required to connect it to a router instead of directly to a computer. The order of powering on the devices is important, because of how they “obtain” their IP addresses, but you don’t have to login and enter a special configuration for the cable modem. With both the cable modem and router (can be a wireless router) turned off, power on the cable modem. After 10 – 30 seconds, it should cycle through its sequence of lights and have obtained a live, global IP address from the residential IP network. At that point, turn on the router (often by plugging it into AC power.) Make sure the ethernet cable (network cable) you are using plugs from the cable modem into the “Internet port” of the router. After it cycles on, you should be able to directly connect/plug computers via a hard-wired Internet connection to the router to get online, and connect wirelessly through the wireless router to get online. I’ll discuss security configuration of the wireless router in a minute, but first want to address DSL modem and router configuration differences.
DSL modem connection
DSL modems come in many flavors, so what I am about to describe here may not apply to you, but the DSL connections I’ve worked with here in the central US have used this configuration. DSL modems I have worked with use the PPPOE (Point-to-Point Protocol over Ethernet) connection method. This means lots of technical things, but practically speaking for a home user wanting to connect through a router to the Internet, it means that a username and password is used to get the modem online. This weekend I was briefly mystified when I was able to directly connect a router to a DSL modem (actually a Speedstream model similar to the one pictured below) and briefly get a hard-wired desktop computer as well as three wireless laptops online– but later the same evening, none of the computers would get online any more.
The problem was that the DSL modem could only handle/permit two or three computers to connect directly through it to the Internet, when it was configured for PPPoE. After some assistance from a very helpful DSL technical support technician on the phone, I learned that it was necessary to reconfigure the DSL modem and take it out of PPPoE mode and into “bridge mode.” I did this by entering the IP address of the DSL modem into the web browser of a computer directly connected (with a wired ethernet cable) to the DSL modem. In this case, that local IP address (192.168.0.1) was helpfully printed on a sticker on the back of the DSL modem. Under the Advanced configuration tab, I was able to change the setup from PPPoE to Bridged Mode.
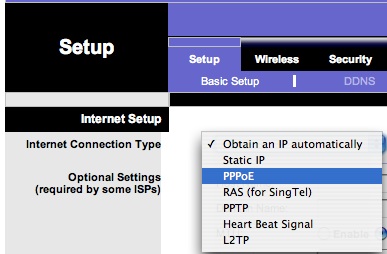
After making that configuration change, I plugged the computer into the wireless router and entered the configuration utility (again by entering the IP address of the device into a web browser of a computer directly connected to the routher: this time 192.168.1.1 for the LinkSys model we were using.) On the initial setup screen, the router allowed me to select PPPoE:
Then, I entered the userid and password of my friend’s DSL account and saved that setting onto the router. At that point, I was able to turn off both the DSL modem and the router, plug the DSL modem directly into the “Internet” port of the router, and power them both on: Again the modem first, and then the router. Whoa-la! The wired and wireless computers in the house could now access the Internet directly– and there was effectively no limit to the number of wireless computers that could get online. (There are just 4 wired ports on the router model we were using, but unless you change the router configuration I think it permits something like 300 wireless clients to connect to it simultaneously.)
Wireless router security configuration recommendations
Wireless routers obtained directly from some ISP’s are now coming with wireless security enabled by default. I have found some wireless DSL modems are enabling WPA wireless security and including the default password for wireless computers to use on a sticker on the bottom of the router. In the case of store-bought wireless routers, however, most come out of the box without ANY wireless security enabled, and as mentioned previously, this can be a problem.
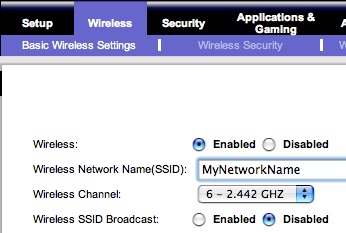
The main disadvantage to enabling wireless security on any network is that connection speeds are reduced because of the security encryption and unencryption taking place. Residential high speed connections are getting pretty fast, and this may not be noticeable, but for people who want as fast a connection as possible (and have high speed connections– today these are mostly cable rather than DSL) over 10 MBPS, this may be an issue. A very basic way to provide some level of security for your wireless network, and prevent casual wireless Internet users from hopping onto your network and “borrowing” your connection, is to hide the name of your wireless network that is by default “broadcast” out to everyone. This is called your SSID, and you can disable SSID broadcast in your wireless router configuration settings:
Once saved, you can manually enter the name of your network into your wireless computer (whether it is running Windows, Mac OS X or Linux) and get online without entering any type of password. This is a pretty good solution to the issue of anonymous neighbors getting onto your high speed connection without permission IMHO, but this is not a true “security” setting for your network that will prevent saavy users who have tools that reveal the names of hidden as well as public wireless networks in their area from borrowing/using your connection.
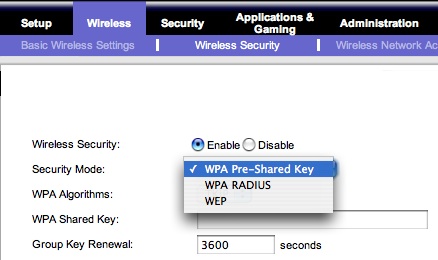
A better choice (but one which will slow down connection speeds for wireless clients) is to enable some type of wireless security on the router. WEP security is very common, but unfortunately is NOT very secure if someone who is an actual hacker tries to gain access to your network. The security recommendations I have read and listened to most recently recommend WPA security over WEP. Depending on the type of wireless router you are configuring, this may be called “WPA Pre-shared Key” security:
A disadvantage (or advantage, depending on your perspective on passwords) of using WPA security is that you will need to use a password that is fairly long, and therefore relatively more secure. This can be a pain when you are sharing the password with friends who bring their laptop over to your house and want to get online, but not too much trouble once it’s entered into the laptop because it should be saved/cached for future use. If you’re wanting to generate a very secure password to use on your home wireless network, check out Steve Gibson’s free password generator on his GRC website. (Along with Leo Laporte, Steve is the guy who does the Security Now! podcast.)
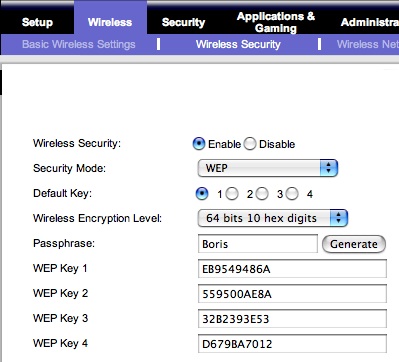
If you use WEP security, one advantage is that you can use a shorter and simpler passphrase. (i.e. a word in English, like the name of your dog or cat.) From a security standpoint, however, this is less secure. If you are connecting with a Windows-based computer, you may be able to use that passphrase to connect to the network, however Macintosh computer clients may require a hexadecimal equivalent of the passphrase. Thankfully, newer wireless routers (and newer versions of router firmware, which you can generally download from the manufacturer’s website and subsequently install) will automatically generate the hex equivalents of WEP passphrases. Click the GENERATE button after entering a passphrase on the Linksys wireless router security configuration page to create these hex equivalents, then use one of them on your Macintosh laptop to connect to the network:
You may need to use the 2nd or 3rd WEP security connection options for Airport if you are using Mac OS 10.3– that’s what we did on my friend’s computer this weekend.
This discussion of residential high speed Internet connection options and recommendations is not intended to be exhaustive, but I hope someone out there finds it helpful. Personally, I find that the more I blog about things like this, the more I personally “own” the ideas and am able to remember them later. Also, I am finding it helpful to refer back to notes like this I’ve blogged in the past– and it can be handy to share the link to something like this with others who want more info on a topic.
Good luck in your own home networking, and best wishes for a future of safe computing! 🙂




Comments
4 responses to “Tips for home high speed Internet connections”
http://linux.softpedia.com/get/System/Operating-Systems/Other/Linux-on-the-Linksys-wrt54g-16921.shtml
Hey Wes,
If you are interested in testing the 2 minute theory (I’ve never heard that stat), find (you’ll have to look hard) a copy of HoneyD or LaBrea tarpits, and throw the meat out on a DMZ. I had a friend do it and he said it took about a day before it was pulverized.
The easiest way (for me) to get around the port 25/110 blocked by Cox Cable is to reconfigure my internet email server (and my Outlook client) to use ports other than 25 & 110. You’d be surprised how many ports are still left open by Cox cable here in Lubbock. If you really are working with a very narrow range of open ports, or if you are really concerned about getting footprinted/fingerprinted by scanners and you have FTP or SMTP servers at home, you can get a Linksys (looks like you have a WRT54G?) to do cool things like NAT-ing an incoming outgoing port to a redirected internal port at an IP of your choosing. Here’s how:
First flash your WRT54G (like I did, remember the one I showed you?) with a Linux based ROM which will give you finer granular control over NAT (and other) settings, such as RADIUS, inetd, syslog, etc. Read this for an overview: http://www.wi-fiplanet.com/tutorials/article.php/3562391 Bottom line, there are lots of different ROMs (little Linux OS’s, custom made for the hardware on the WRT54G, and free) out there, so just pick one. Here’s one I just found, which purports to have SNORT http://linux.softpedia.com/get/System/Operating-Systems/Other/Linux-on-the-Linksys-wrt54g-16921.shtml
By the way, SNORT is a very cool IDS (http://www.snort.org/), a cool alternative to a tarpit if you want to stay far clear of behavior some people might question.
That’s a great primer for folks who are new (or not even new) to using a home wireless router. I’m always amazed when I talk to someone who has a wireless router set up at their house with NO protection turned on at all!
I’ve got a very similar setup, also using a WPA key. Two other (small) items to add — when choosing an SSID, don’t use something obvious (like “Rich’s House”) or your street address. It never hurts to keep that SSID a little bit more vague even after you turn off the broadcast of the name. Second, I like to use MAC address filtering, since I just have one laptop so it’s not a problem to keep that single MAC address in the configuration.
Now of course determined crackers can get past the hidden SSID, and they can spoof MAC addresses — but anything to make their job harder will help to deflect them to someone else’s router!
Glad to hear that you listen to Steve Gibson and Leo Laporte – that’s one netcast that I never miss. Steve’s “Shields Up” free port scan is one tool that I really like to use for my own home network, as well as my school’s network (I’m the technology coordinator).
Rich